OpenLDAP is an open source implementation of LDAP or Lightweight Directory Access Protocol . OpenLDAP allows to store store and organize user related data centrally. OpenLDAP functions like a relational database & can store any data but its normally used as a address book. Its used for authenticating and authorizing of the users. Information stored in OpenLDAP is in hierarchical manner & We can group the users into a single or multiple groups based on necessity.
In this tutorial, we will learn to install & configure LDAP with OpenLDAP, step by step.
(Recommended Read: Beginner's guide to implementing DNS server using BIND )
LDAP Installation
All the OpenLDAP packages are available with default package repositories, we need to install ‘openldap’, ‘openldap-clients’ & ‘openldap-servers’ packages. Install them using the following command,
[root@ldap ~]# yum install openldap openldap-clients openldap-servers
Once the packages have been installed, we will create password for ldap administrative user with the following command,
[root@ldap ~]# slappasswd
New password:
Re-enter new password:
{SSHA}dMKRmlKAM5YumREa5/TWrd98zwZTBE0c
We will need the encrypted password, so make a note of that. Now start the ldap server & enable it for boot,
$ systemctl start slapd
$ systemctl enable slapd
Configure LDAP
We will configure LDAP server using the configuration file for OpenLDAP, named ‘olcDatabase={2}hdb.ldif’ located at ‘/etc/openldap/slapd.d/cn=config’. Open the file,
[root@ldap ~]# cd /etc/openldap/slapd.d/cn=config
[root@ldap ~]# vi olcDatabase={2}hdb.ldif
& edit the following two lines to match your domain,
olcSuffix: dc=linuxtechlab,dc=local
olcRootDN: cn=Manager,dc=linuxtechlab,dc=local
& add the following line to the file.
olcRootPW:{SSHA}dMKRmlKAM5YumREa5/TWrd98zwZTBE0c
here, ‘olcSuffix: dc=linuxtechlab,dc=local’ is used to define the your preferred domain, which in our case in ‘linuxtechlab.local’ & with ‘’olcRootPW’, we have defined the administrator password for Domain admin.
Next make the changes in file ‘/etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif’ to make it as per domain,
[root@ldap ~]# vi /etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=extern
al,cn=auth" read by dn.base="cn=Manager,dc=linuxtechlab,dc=local" read by * none
Save the file & exit. Now run the slaptest to make sure that the configurations made are correct,
[root@localhost ~]# slaptest -u
59fbb825 ldif_read_file: checksum error on "/etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif"
59fbb825 ldif_read_file: checksum error on "/etc/openldap/slapd.d/cn=config/olcDatabase={2}hdb.ldif"
config file testing succeeded
If you receive any checksum errors, forget about them. Make sure that config testing succeeds.
Setting up LDAP Database
After making the above mentioned configurations, we will now setup a database for OpenLDAP server.
There is a sample ldap database configuration file located in ‘/usr/share/openldap-servers’, we will use it as reference as our database file. Copy the file to ‘/usr/lib/ldap’ with the following command,
[root@ldap ~]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG [root@ldap ~]# chown ldap:ldap /var/lib/ldap/*
Once done, add the following files to the ldap schema,
[root@localhost ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
[root@localhost ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
[root@localhost ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
Next we need to generate a file named ‘base.ldif’ which will contain information regarding our OU,
[root@localhost ~]# vim /root/base.ldif
dn: dc=linuxtechlab,dc=local
dc: linuxtechlab
objectClass: top
objectClass: domain
dn: cn=ldapadm ,dc=linuxtechlab,dc=local
objectClass: organizationalRole
cn: Manager
description: LDAP Manager
dn: ou=Employees,dc=linuxtechlab,dc=local
objectClass: organizationalUnit
ou: Employees
dn: ou=Visitors,dc=linuxtechlab,dc=local
objectClass: organizationalUnit
ou: Visitors
Now build the directory structure with the following command,
[root@localhost ~]# ldapadd -x -W -D "cn=Manager,dc=linuxtechlab,dc=local" -f /root/base.ldif
you will than be asked to enter the root password for LDAP. Upon successful authentication, you should get the following output ,
adding new entry "dc=linuxtechlab,dc=local"
adding new entry "cn=ldapadm ,dc=linuxtechlab,dc=local"
adding new entry "ou=Employees,dc=linuxtechlab,dc=local"
adding new entry "ou=Visitors,dc=linuxtechlab,dc=local"
Our OpenLDAP server is almost complete, we now only have to add some users to our LDAP server. We now will create two users, one named ‘sara’ for our OU named ‘Employees’ & other named ‘Dan’ for OU named ‘Visitors’,
[root@localhost ~]# vi /root/sara.ldif
dn: uid=Sara,ou=Employees,dc=linuxtechlab,dc=local
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: sara
uid: sara
uidNumber: 800
gidNumber: 101
homeDirectory: /home/sara
loginShell: /bin/bash
gecos: Sara
userPassword: {crypt}x
shadowLastChange: 17058
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
These are only temporary files & can be deleted after they have been exported to OpenLDAP database or you can keep them as reference to add new users. Next we add the new user in LDAP,
[root@localhost ~]# ldapadd -x -W -D "cn=Manager,dc=linuxtechlab,dc=local" -f /root/sara.ldif
Enter the root LDAP password & you should get the following output upon successful authentication,
adding new entry "cn=Sara Smith,ou=Employees,dc=linuxtechlab,dc=local"
Next we will assign this user ‘sara’ a password with the following command,
[root@localhost ~]# ldappasswd -s Sara@123 -W -D "cn=Manager,dc=linuxtechlab,dc=local" -x "uid=sara,ou=Employees,dc=linuxtechlab,dc=local"
Similarly add the more users. Perform a ldap search after all the users have been added to make sure that all users have been added successfully, use this command,
[root@localhost ~]# ldapsearch -x cn=sara -b dc=linuxtechlab,dc=local
Adding Ldap authentication to a remote machine
Now that we have our OpenLDAP ready with some users configured, we will add the ldap authentication to a remote machine & will use our LDAP users for logging into the system. Firstly open the terminal on remote machine & install the following packages to install OpneLDAP client on the machine,
$ yum install -y openldap-clients nss-pam-ldapd
Once the packages have been installed, run the following command to configure the LDAP authentication,
$ authconfig-tui
& configure the ldap authentication as shown in pictures below,
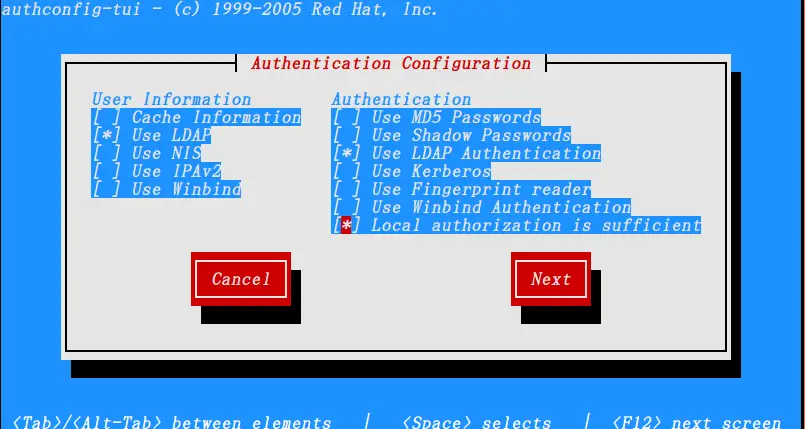
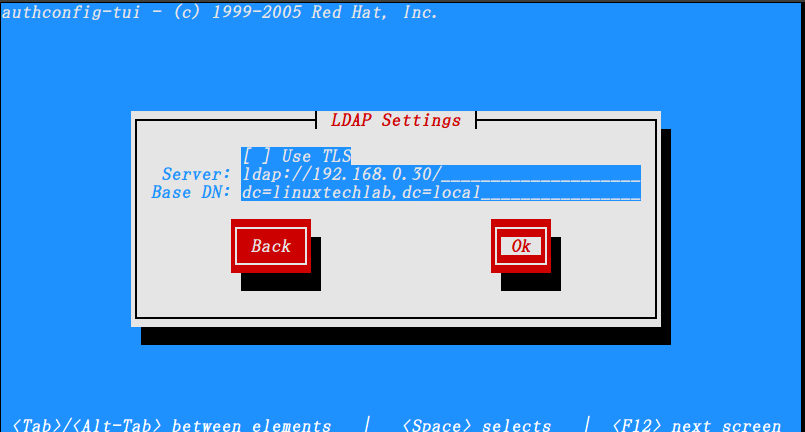
Once done, you can check if the configuration have been successfully or not by using the following command,
$ getent passwd sara
If configurations have been made correctly, you should get the following output,
sara:x:800:101:Sara:/home/sara:/bin/bash
That’s it , we can now use the ldap users to login to the remote machines. With this we end our tutorial on how to install & configure LDAP server on CentOS 7, please feel free to send out your questions using the comment box below.
If you think we have helped you or just want to support us, please consider these :-
Connect to us: Facebook | Twitter | Google Plus
Donate us some of you hard earned money: [paypal-donation]
Linux TechLab is thankful for your continued support.

that’s what i was looking for , thanks !!
Waht I’d REALLY love to see is a somewhat more advanced tutorial on how to setup LDAP as both an authentication source AND a shared address book…. Or even JUST an address book. I’ve never seen the address book function documented.
Thanks Bruce for your suggestion. Will certainly see if can cook something up.
Hi – Tried this but cannot seem to store to the attributes within the inetorgperson schema? E.g. mail, sn, givenName etc
Any thoughts?
Well it should work & it was tested. Can you please share the exact error you are getting.
Why am I getting the error? Appreciate your help on this/
”
[root@myServer cn=config]# ldapadd -x -W -D “cn=Manager,dc=myServer,dc=local” -f /root/base.ldif
Enter LDAP Password:
ldap_bind: Invalid DN syntax (34)
additional info: invalid DN
“
It can occur due to many reasons, most probably something is wrong with your config file. Double check all the config files & try again.
You need to write quotes manually, if you copy the command from here it won’t work.
See the difference between ” and ” 🙂
This fixed it for me.
Hey thanks for informing, will edit it.
I’m getting the same error as Bharathan getting:
[root@localhost ~]# ldapadd -x -W -D “cn=Manager,dc=linuxtechlab,dc=local” -f /root/base.ldif
Enter LDAP Password:
ldap_bind: Invalid DN syntax (34)
additional info: invalid DN
[root@localhost ~]#
Please help!
Have you made multiple entries for OU etc in the config files, if yes those needs to separated with a blank line. Also some of users have reported that removing & reinstalling from scratch have solved the issue for them.
Try these suggestions & if this does not work, maybe send the complete config files to check properly.
I receive the same error. What should i do? I’m trying to config on a Centos 7 VM deployed on vSphere
Can you please elaborate on which error you are referring to.
i did the same steps and i didn’t get any errors but when i try to test it on the client machine nothing shows how can i can know where the error is please
can you please let me know the exact error to help you better with the query.
It’s ok. I managed to create the LDAP. Thanka
Hi. I’m getting an error when adding the Manager to base.ldif.
error : ldap_bind: Invalid credentials
I followed the steps correctly, do you know whats going on?
Can you please mention the complete command that you executed when you get this error .
Works 90% great! Only part I’m stuck on is the client-passwd command. User executes “passwd” command and all *appears* to work well until the end where I get errors below. Any ideas?
$ passwd
Changing password for user testuser.
(current) LDAP Password:
New password:
Retype new password:
password change failed: Invalid credentials
passwd: Authentication token manipulation error
Thx!
I tried to reproduce this but unable, could you please provide more information like did you make any changes with respect to tutorial ?
Pretty much right on the tutorial except for name changes. I’m thinking I should start over.. perhaps I made a typo that affected the outcome. Thank you for the confirmation that you’re not having problems with the passwd command; that’s important. – Rich
try it again & let us know if something comes up..
I believe I’ve found the solution. In my case it was the way the quotes around “cn=Manager,dc=myServer,dc=local” are formatted on this site, assuming you’ve copied and pasted. Try deleting the the double quotes either side and retype them. Hope this helps – Matt
thanks much it worked for me
just when we creat vim /root/base.ldif we should put empty lines before dn:
ex:
objectClass: top
objectClass: domain
dn: cn=ldapadm ,dc=linuxtechlab,dc=local
objectClass: organizationalRole
cn: Manager
Slaps service is not starting
What’s the error ??
You should not be using an editor to modify the files in the cn=config database. The correct methodology is to use the ldap* utilities (such as ldapmodify, etc). Alternatively, one can use slapcat to export the config DB to an LDIF file, and slapadd to import it (for example, to change from the deprecated back-hdb to the supported back-mdb database backend).
For example, to change the suffix of the database:
ldapmodify -H ldapi:/// -Y EXTERNAL
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=example,dc=com
I configured the LDAP server and LDAP client.
I am successfully login with su command from LDAP client.
Also I tested “ldapsearch ” with password from LDAP client to login to the LDAP server.
All got successful, as shown below.
===========
From LDAP Client host
==================
root@rpcentosbuild /root [03:28:18 PM] 0j
# ldapsearch -x -D “uid=ravi,ou=Employees,dc=my-domain,dc=com” -W -H ldap://10.55.21.169 -b “ou=Employees,dc=my-domain,dc=com” -s sub ‘uid=ravi’
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: uid=ravi
# requesting: ALL
#
# Ravi, Employees, my-domain.com
dn: uid=Ravi,ou=Employees,dc=my-domain,dc=com
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: ravi
uid: ravi
uidNumber: 800
gidNumber: 101
homeDirectory: /home/ravi
loginShell: /bin/bash
gecos: Ravi
shadowLastChange: 17058
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
userPassword:: e1NTSEF9MERvWXFOU1VLT0wrZ2liU2pTZWo4MHcyakZDNitDVVo=
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
================
su login from LDAP client host
======================
root@rpcentosbuild /etc/pam.d [04:04:41 PM] 0j
[1]# su – ravi
Last login: Tue Nov 20 09:24:05 IST 2018 on pts/3
Last failed login: Tue Nov 20 15:02:33 IST 2018 from 10.55.171.78 on ssh:notty
There were 11 failed login attempts since the last successful login.
/usr/bin/id: cannot find name for group ID 101
-bash-4.2$ id
uid=800(ravi) gid=101 groups=101
How can I login with the “my-doamin.com\ravi” as a user.
I have to thank you for the efforts you have put in writing this
site. I am hoping to view the same high-grade blog posts from you
later on as well. In fact, your creative writing abilities has motivated me to get my own, personal website
now 😉
When I’m processing the base.ldif I’m getting the following message:
ldap_bind: Invalid DN syntax (34)
additional info: invalid DN
Can’t seem to figure out why.
Gene
Can we connect this centos ldap sever with Ubuntu client??
yes, we can & will soon be publishing article addressing the same.
Please can anyone help me out to resolve the issue with the credentials, Despite Entering the Hashed credentials i am facing the following error
ldap_bind: Invalid credentials (49)
systemctl restart slapd
I have problem connection from client ldap to server when i have sha or ssha password encoded but when i have crypt endoded password user i can do log using ldap database.
So I’m able do ldapsearch from client with auntentication with password from ldap with sha password encoded for this user but i can’t login on client machine using the same password like ldapsearch.
Thank you VERY MUCH! I’ve looked all over the web, and either the directions don’t work, or they’re difficult to follow, or they’re not directly meeting my needs. Thank you thank you!!!!!
hi when i try i get this error please help me
I’m getting the same error as Bharathan getting:
[root@localhost ~]# ldapadd -x -W -D “cn=Manager,dc=lvenkey,dc=xyz” -f /root/base.ldif
Enter LDAP Password:
ldap_bind: Invalid DN syntax (34)
additional info: invalid DN
[root@localhost ~]#
Everything is working fine but the problem arrived when I restarted slapd service. When i search for user in LDAP database after restarting it show there is no entry.
I have a virtual machine (Redhat 7), and I followed your steps to the letter. What I would like right now is to connect to this server from a Windows client. Problem is, I’m unable to.
Even when I do: telnet ldap://127.0.0.1 389, I get an error.
In the server side, the status of ldap is clearly running:
slapd.service – OpenLDAP Server Daemon
Loaded: loaded (/usr/lib/systemd/system/slapd.service; enabled; vendor preset: disabled)
Active: active (running) since Fri 2020-02-21 15:31:17 CET; 1h 20min ago
Docs: man:slapd
man:slapd-config
man:slapd-hdb
man:slapd-mdb
file:///usr/share/doc/openldap-servers/guide.html
Process: 8595 ExecStart=/usr/sbin/slapd -u ldap -h ${SLAPD_URLS} $SLAPD_OPTIONS (code=exited, status=0/SUCCESS)
Process: 8557 ExecStartPre=/usr/libexec/openldap/check-config.sh (code=exited, status=0/SUCCESS)
Main PID: 8597 (slapd)
CGroup: /system.slice/slapd.service
└─8597 /usr/sbin/slapd -u ldap -h ldapi:/// ldap:///
Feb 21 16:36:51 SLNXPTXSHVRA646 slapd[8597]: conn=1019 fd=13 ACCEPT from IP=127.0.0.1:51476 (IP=0.0.0.0:389)
Feb 21 16:36:51 SLNXPTXSHVRA646 slapd[8597]: conn=1019 op=0 EXT oid=1.3.6.1.4.1.1466.20037
Feb 21 16:36:51 SLNXPTXSHVRA646 slapd[8597]: conn=1019 op=0 STARTTLS
Feb 21 16:36:51 SLNXPTXSHVRA646 slapd[8597]: conn=1019 op=0 RESULT oid= err=0 text=
Feb 21 16:36:51 SLNXPTXSHVRA646 slapd[8597]: conn=1019 fd=13 closed (TLS negotiation failure)
Feb 21 16:36:55 SLNXPTXSHVRA646 slapd[8597]: conn=1020 fd=13 ACCEPT from IP=127.0.0.1:51478 (IP=0.0.0.0:389)
Feb 21 16:36:55 SLNXPTXSHVRA646 slapd[8597]: conn=1020 op=0 EXT oid=1.3.6.1.4.1.1466.20037
Feb 21 16:36:55 SLNXPTXSHVRA646 slapd[8597]: conn=1020 op=0 STARTTLS
Feb 21 16:36:55 SLNXPTXSHVRA646 slapd[8597]: conn=1020 op=0 RESULT oid= err=0 text=
Feb 21 16:36:55 SLNXPTXSHVRA646 slapd[8597]: conn=1020 fd=13 closed (TLS negotiation failure)
What am I missing?
Hi,
Thanks for turotial.
I see error while running systemctl command. Any suggestions on how to fix it.
[root@devservcer0001 ~]# systemctl start slapd
Job for slapd.service failed because the control process exited with error code. See “systemctl status slapd.service” and “journalctl -xe” for details.
Hello,
Thanks for the tutorial.
Do you have any advance guides or tutorials for managing Openldap? I am looking for guidance on customizing the ldap schema. I have been successful with creating custom attributes and objects, but I am having trouble with creating custom distinguished names. When I attempt to add an ldap entry (using ldapadd) with something other than the standard DN values, I receive the following error message:
ldap_add: Invalid DN syntax (34)
additional info: invalid DN
Any help will be greatly appreciated.
I will be creating one soon.